Abstract
As humans, we are very good at processing information quickly and making decisions based on that information. But unfriendly individuals online may take advantage of these factors that make us human by encouraging us to make fast decisions, such as responding to urgent-sounding messages. This article explains the concepts of our intuitive (fast) and rational (slow) decision-making processes. It also discusses a common approach that unfriendly online individuals use in their attempts to hack or gain access to our smart phones or computers and capture our personal information. Finally, readers will learn how mindfulness can help them slow down and be present in the moment, which will help them to decide how best to respond, if at all, to the information they receive online.
Learning From Experiences
What factors make us human? These factors include our ability to think, feel, process information, make decisions, and learn from the choices we make. Our human factors help us to make sense of what we are seeing and how we interact with each other and with machines. Imagine you want to cross a street. You learned when you were small never to step into the street without checking first for oncoming cars. That is, you were taught to stop, be mindful of approaching cars, and then cross the street only after deciding it was safe. Once you crossed the street successfully without harm, you learned that this approach worked, and you should repeat it again. If you learned these safety steps as a child, then this knowledge came from personal experience and the wisdom you gained from that experience. Knowledge gained from personal experiences comes from our thinking and decision-making processes, and the consequences we experience.
Two Ways of Thinking
Imagine you are at a fork in the road, and you can either take the shortcut or go the long way. Similar to a fork in the road, we tend to rely on two general types of thinking paths, called Type I and II. These thinking paths help us decide which direction to choose in many situations, including when we are online. One of our thinking paths is fast (intuitive), and the other is slow (rational), and both paths have both positive and negative outcomes (Figure 1). These two thinking paths help us to reason and make judgments and decisions [1, 2].
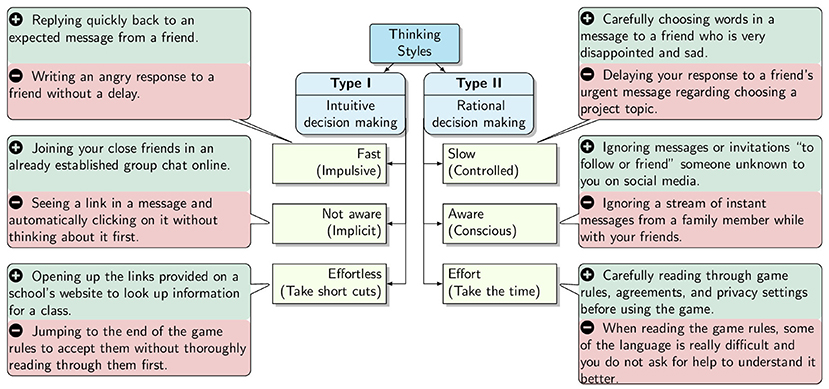
- Figure 1 - Both intuitive and rational decision making having pros and cons, as shown in the example here in green and red, respectively.
Type I thinking tends to be fast, automatic, and almost effortless. With Type I thinking we are not consciously aware of the information we are receiving and processing. Type I thinking involves intuitive decision making, which is also known as our “gut feeling” decisions. For example, if a car were speeding toward you, Type I thinking and intuitive decision making would help you automatically move out of the way. However, let us say your friend posts an unpleasant message about you in a group chat. How would you respond? Would you decide quickly and respond defensively, going with your gut feeling? Or would you stop and consider that, instead of posting an angry response, you could talk directly to your friend about the post? This decision to stop and think about the best way to respond, if at all, is Type II thinking.
Type II thinking is controlled, and we are aware or conscious of this type of thinking. Type II thinking involves rational decision making, in which we take time and effort to assess and compare the information we have from our prior experiences (i.e., what to do before crossing the road). When using Type II thinking to make a decision, you may analyze the pros and cons of each possible outcome. You may also consider your belief system, which includes the truths that you accept about yourself. Similarly, your values, meaning what is important to you that influences and guides your behavior, can also play a role in this type of thinking.
For example, do you value safety more highly than you value taking risks? Imagine you are thinking of posting your picture online. Before doing so, you may try to figure out how your family or friends would react. To do this, you would most likely use a mental model to fill in or guess any missing information. Making a mental model is also part of Type II thinking. Think of it like a puzzle with missing pieces: you make a mental model to complete the puzzle, even if the pieces are not available. Completing the puzzle gives you a better idea how your friends and family would respond to your photo online.
To summarize, with rational decision making, we take our time to evaluate each option, use mental models to fill in missing information, and use our prior knowledge to help us decide. Figure 1 illustrates how our two thinking paths and decision-making processes can affect us both positively and negatively when online.
How Can Human Factors Contribute to Cyberattacks?
Now you know a bit about each thinking path and how each path affects your decision making. So, when we are online, why do we sometimes not pay attention to the warning signs in cyberspace? When you are online (in cyberspace), do you stop to consider your choices, or do you make quick decisions instead? Cybersecurity research has shown that when we do not focus on the information presented and instead make a choice intuitively (using Type I thinking), we have a greater chance of experiencing a negative consequence. A report from the World Economic Forum identified that 95% of cyberattacks are related to human factors (i.e., the decisions we make) [3]. Consequences from such decisions can include businesses losing control of their computers and people losing money [3]. Like in the real world, not everyone is friendly online. Some unfriendly individuals are interested in finding our weak or vulnerable spots from our online posts so they can gain access to our personal information. By targeting our emotions or catching us when we are not focused, unfriendly online individuals encourage us to respond quickly and decide intuitively. Unfriendly online individuals have found that getting others to use Type I thinking is a successful way to access people’s private information [4]. This type of cyber-targeted technique is called social engineering. Social-engineered messages sound urgent, like something serious has happened.
These messages make us feel we should respond immediately, without thinking about it first. A socially engineered cyberattack targets our basic psychological needs, including our interest in trusting and helping others and our need for love, acceptance, and belonging. These attacks take advantage of our ways of thinking, making decisions, and behaving, as well as our willingness to pay for something of value. For example, a person may receive a message that a family member was in an accident, and a payment is urgently needed for their medical care [4].
In short, unfriendly online individuals want us to use our intuitive decision making and respond impulsively. Remember: how you decide to respond to the information you receive online (i.e., a request to post your picture or to respond to an unpleasant chat message) can result in a positive or negative outcome. Figure 2 gives an example of friending someone online who then asks for your personal information. What would you do?
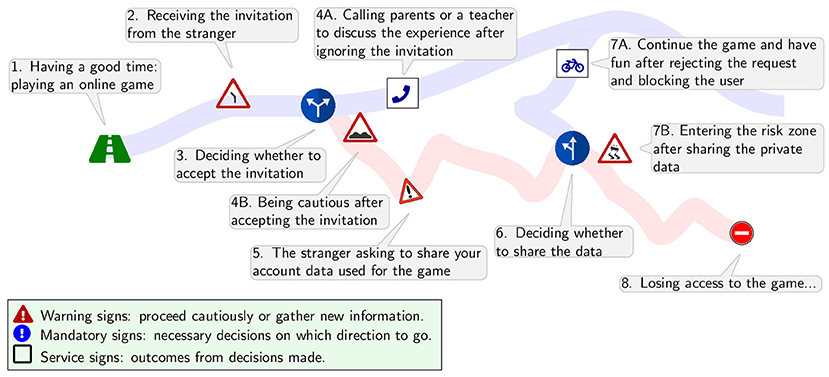
- Figure 2 - Online decision making represented by common traffic signs seen along the road (Icons designed using Freepik).
Supporting Decision Making to Avoid Cyberattacks
Metacognition means thinking about the way you think. You could call metacognition your command-and-control center for organizing and managing your information and knowledge [5]. Examples of metacognition include realizing that you are using an easy way to solve a math problem, like trying random numbers, or noticing that you are focused on the rain tapping on the window instead of the actual math problem. You can use your metacognition to change your way of thinking and bring your attention back to the math problem. Thus, metacognition helps with many things, including planning, figuring out what information is missing, using knowledge from past experiences and evaluating the outcome from the choice made (what did I learn from this?). Metacognition can also help you understand how your decisions change when you feel upset or stressed, which can help you stop yourself from deciding at that time [5].
In short, metacognition is a great tool to help us avoid acting impulsively, such as by choosing not to respond immediately to an unpleasant online message [5]. Metacognition makes us aware of the warning signs, nudges us to slow down, encourages us to think about the information presented, and helps us evaluate which direction to go.
Using Mindfulness to Prevent Cyber Attacks
Mindfulness helps you be present in the moment, such as by noticing how you are feeling. It involves observing what is happening around you (what you are seeing) and reflecting on what it all means (assessing the situation). Mindfulness helps you pause before making a decision.
From what you have learned about Type I and II thinking and how some unfriendly online individuals may try to harm us in cyberspace, it is easy to see how, when we are distracted or upset, we can slip and give away our information. Although we cannot prevent all slips, we can try to slow down and become mindful, reducing the chances of negative outcomes from fast online decisions. Creating your own mindful decision-making streetlight, with red, yellow, and green lights, can help you ask yourself some key questions and decide what to do (Figure 3). Before making any decisions, it is always a good idea to double check with a family member or teacher about any emails, posts, or online requests that seem strange.
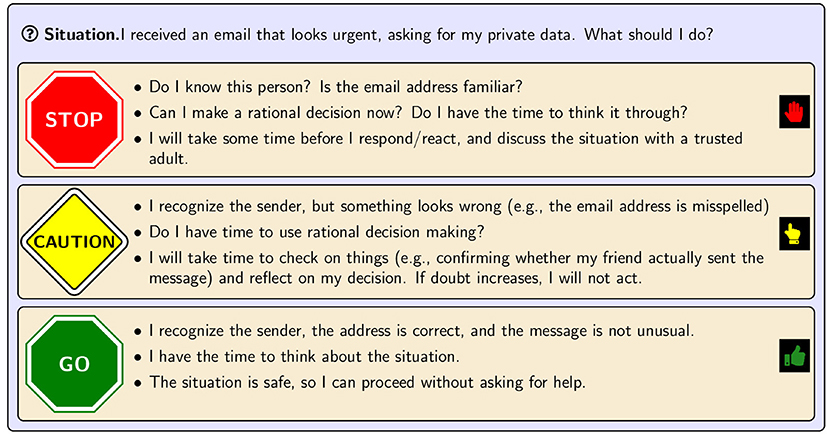
- Figure 3 - A mindful decision-making streetlight can help you make the best decisions when you are confronted with unusual information or requests online.
In summary, unfriendly online individuals use socially engineered messages to try to gain access to our personal information. Socially engineered messages encourage us to make intuitive decisions and to respond impulsively so we will not realize what information we are giving away. Both metacognition and mindfulness can help us pause, reflect on what we are observing and prevent us from automatically reacting to urgently sounding messages online. Finally, it is important to understand that whatever you post online, even in a private chat with friends, leaves a “digital footprint”—a personal information trail about you. Therefore, being mindful of what you do online will help you make the right decisions and keep you safe.
Glossary
Intuitive Decision Making: ↑ Making decisions based on our “gut feelings.” These decisions are made quickly and effortlessly, and we are not consciously aware of them.
Rational Decision Making: ↑ Making decisions slowly and consciously, to deliberately assess the pros and cons of each option.
Mental Model: ↑ A mental framework used to fill in information that is not available. By placing the missing information in a model, a person can anticipate what outcomes or events could happen.
Cybersecurity: ↑ The practice of protecting and preventing unauthorized individuals from illegally accessing the sensitive data contained on internet-connected computers or networks.
Social Engineering: ↑ An online attempt to target a person’s emotions and psychological needs, such as an urgent-sounding message that encourages people to respond immediately without thinking it through first.
Metacognition: ↑ Is our ability to be aware of our thinking and learning processes. Metacognition helps us plan, monitor and self-correct our thinking, and helps us evaluate the learning outcomes.
Mindfulness: ↑ A technique that helps us to be present in the moment, aware of what we are doing, and able to pause and reflect on our thoughts and decisions without judgment.
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Acknowledgments
The authors thank their families for their friendly feedback and support in the journey of the paper preparation.
References
[1] ↑ Evans, J. S. B. T., and Stanovich, K. E. 2013. Dual-process theories of higher cognition: advancing the debate. Perspect. Psychol. Sci. 8:223–241. doi: 10.1177/1745691612460685
[2] ↑ Strack, F., and Deutsch, R. 2004. Reflective and impulsive determinants of social behavior. Person. Soc. Psychol. Rev. 8:220–247. doi: 10.1207/s15327957pspr0803_1
[3] ↑ Alsharif, M., Mishra, S., and AlShehri, M. 2022. Impact of human vulnerabilities on cybersecurity. Comput. Syst. Sci. Eng. 40:1153–1166. doi: 10.32604/csse.2022.019938
[4] ↑ Nurse, J. R. C. 2019. Cybercrime and you: how criminals attack and the human factors that they seek to exploit. In: Attrill-Smith A, Fullwood C, Keep M, Kuss DJ, editors, The Oxford Handbook of Cyberpsychology (Oxford: Oxford University Press), 663–690. doi: 10.1093/oxfordhb/9780198812746.013.35
[5] ↑ Flavell, J. H. 1976. Metacognitive aspects of problem solving. In: Resnick LB, editor, The Nature of Intelligence (London: Routledge), 231–236. doi: 10.4324/9781032646527-16
